The RC522 is a cheap RFID module that can read and write Mifare’s tags and being sold at several web stores, like eBay and included with many “starter kits” nowadays. Simply search RFID-RC522 (MF-RC522). The card reader and the tags communicate using a 13.56MHz electromagnetic field. (ISO 14443A standart tags)
Wiring up:
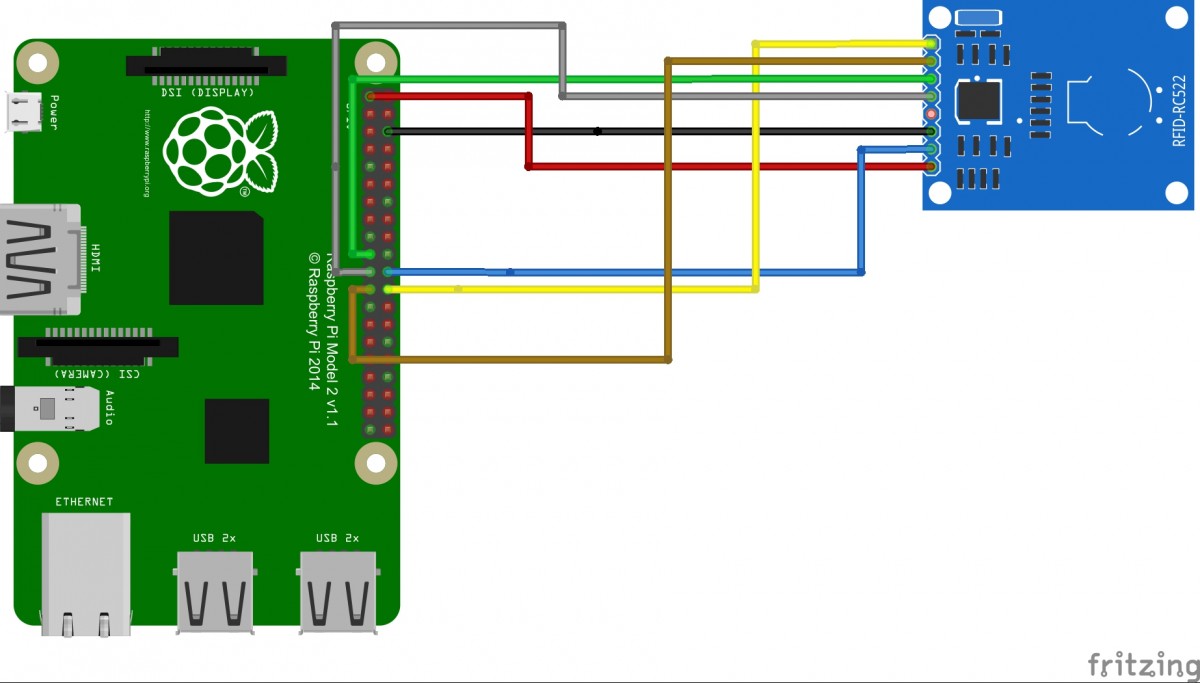
Below table shows the connection between RC522 and RPi2:
| RC522 pin | RPi2 pin nr | RPi2 pin name |
|---|---|---|
| SDA | 24 | GPIO8 |
| SCK | 23 | GPIO11 |
| MOSI | 19 | GPIO10 |
| MISO | 21 | GPIO9 |
| IRQ | Remark: Not connected | |
| GND | GND | GND |
| RST | 22 | GPIO25 |
| 3.3V | 1 | 3V3 |
Please note that the RPi2 has a 40 pin header (RPi1 has 25).
RPi2 steps:
We need to enable all the python libraries and the SPI interface on the RPi2 to get it working.
To install the python environment:
sudo apt-get install python-dev
enable spi interface:
Edit the file /boot/config.txt and add the following two lines:
device_tree_param=spi=on dtoverlay=spi-bcm2708
To check if the SPI interface is working, please reboot the RPi and run the following instructions:
$ dmesg | grep spi
The output will look like:
[ 10.886588] bcm2708_spi 3f204000.spi: master is unqueued, this is deprecated [ 10.901487] bcm2708_spi 3f204000.spi: SPI Controller at 0x3f204000 (irq 80)
Now download and install the SPI python library:
git clone https://github.com/lthiery/SPI-Py.git $ cd SPI-Py $ sudo python setup.py install
Now download and run the RC522 lib:
$ git clone https://github.com/rasplay/MFRC522-python.git $ cd MFRC522-python $ python read.py
The output will look like:
Card detected Card read UID: 98,40,242,197,125